Troubleshooting and debugging IAM policies – Identity and Access Management – Securing Users, Roles, and Policies
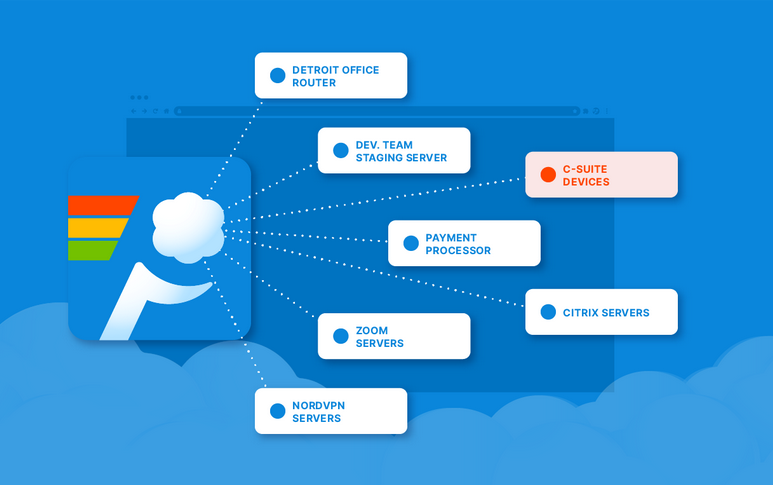
Troubleshooting and debugging IAM policies Despite meticulous planning, there will be times when IAM policies don’t behave as anticipated. AWS CloudTrail is invaluable in these situations. It logs all AWS API calls, providing insights into…